SimpleAuthority is a fully functional Certification Authority (CA) that is designed to be very easy to use. It generates and manages keys and certificates that provide cryptographic digital. .MD5 Encryption with SimpleAuthority. SimpleAuthority has two modes for specifying the password: plain text and MD5 encrypted. The above examples use plain text passwords. To improve security, MD5 is highly encouraged. Message-Digest algorithm is a one-way hash function that generates a 128-bit hash value from an input.
Resources
Commercial support details and some general Java cryptography resources, which you may, or may not, find helpful. If you have an article, book, or project you would like to see added below send a message to feedback-crypto@bouncycastle.org
Complimentary Packages
EJBCA
EJBCA is a fully functional Certificate Authority using J2EE technology. EJBCA builds on the J2EE platform to create a robust, high performance, platform independent, flexible, and component based CA to be used standalone or integrated in any J2EE app.
Novosec Extensions
This package provides the following pure Java extensions to the Bouncy Castle framework and has been made freely available by www.novosec.com:
- OCSP (RFC 2560) server and client
- CMP (RFC 2510, RFC 2511) generator and parser.
JCE taglib
A JSP tag library with cryptographic funtions and X.509 certificate generationbased on BouncyCastle JCE. There is also a refactoring of JCE taglib CryptoLib on the main JCE taglib project page. CryptoLib can also be used with non-JSP projects.
LightCrypto
A library of cryptographic functions based on the lightweight API, includingsome functions for use with HSQLDB embeddable database.
Portecle
Portecle is a user friendly GUI application for creating, managing and examining key stores, keys, certificates, certificate requests, certificate revocation lists and more.
Jasypt - Java Simplified Encryption
Jasypt is a java library which allows the developer to add basic encryption capabilities to his/her projects with minimum effort. It offers transparent integration with Hibernate, an open API for use with any JCE provider, and is suitable for integration into Spring-based applications and ACEGI.Instructions on using it with Bouncy Castle can be found at:http://www.jasypt.org/bouncy-castle.html.
KeyTool IUI
KeyTool is a free user friendly GUI application for creating, managing keys and keystores as an alternative to the JDK's KeyTool command.
SimpleAuthority
A basic free Certification Authority. Can be used to generate keys for Secure email, VPN access and client/server SSL authentication.
Footprint
A set of tools for generating signed PDF documents, as well as certificates.
Commercial Support
If you are reporting a bug, or would simply like to suggest something to add to the library let us know at feedback-crypto@bouncycastle.org and your request will be dealt with, if you need something else read on.
The Legion of the Bouncy Castle is a strictly non-profit, no financial interest organisation, however we do get requests for commercial support or project work from time to time. To deal with this and help fund further work on the APIs we have set up Crypto Workshop If you need a support agreement or have an issue that might need a solution requiring consulting, mentoring, or education, please contact us info@cryptoworkshop.com
Note: As Crypto Workshop is made up of founders to and contributors to Bouncy Castle who have commit access, it is the only source for Bouncy Castle support recognised by the project.
Articles

Simple Authority
English
A Layman's Guide to a Subset of ASN.1, BER, and DER
Burton Kaliski Jr.
Burton Kaliski Jr.'s definitive introduction to ASN.1, BER, and DER - RSA Data Security, Inc. Public-Key Cryptography Standards (PKCS) 1993 edition.
MIDP Application Security 3: Authentication in MIDP
Jonathan Knudsen
Examples of using the lightweight API, brief discussion about obfuscation.
MIDP Application Security 4: Encryption in MIDP
Jonathan Knudsen
More examples of using the lightweight API.
Data security in mobile Java applications
Michael Juntao Yuan
Includes examples of the lighweight API as well as general discussion of other alternatives.
Securing your J2ME/MIDP apps
Michael Juntao Yuan
Includes examples of the lighweight API used for XML signatures.
Français
Cryptographie avec Bouncy Castle
Nyal
Ce tutoriel constitue une première approche pour l'utilisation de la bibliothèque Bouncy Castle.
Utiliser PGP avec Java et Bouncy Castle
Graham Jenkins (Traduction française par Simon Depiets, relecture de la traduction française par Joëlle Cornavin).
Books
English
Java Cryptography: Tools and Techniques
David Hook, Jon Eaves - Leanpub
Written by two founders of the Bouncy Castle project, as a successor to 'Beginning Cryptography with Java', the book will cover the recent features introduced in the JCA/JCE as well the latest changes to the BC APIs and the BCFIPS Java module (first 11 chapters now in place, parts of the remaining chapters (up to 15) as well - make sure you sign up for updates, we release new sections and revisions about once a month).
A copy of the source code for the examples in the book can be found in java-crypto-tools-src.zip.
The following are books listed in association with amazon.com. Any proceeds received from this are used to support the running of this web site.
Beginning Cryptography with Java
David Hook - Wrox
Written by a Bouncy Castle APIs committer, the book covers recent features introduced in the JCA/JCE cryptography APIs in JDK 1.5 and is fully up to date with the cryptography APIs in J2SE 5.01, including Elliptic Curve cryptography, as well as dealing with earlier versions of the JCE/JCA in earlier JDKs. The book also deals with provider installation, X.509 certificate generation, CRL generation, and the creation and processing of PKCS #10 certification requests using the JCA and the Bouncy Castle APIs, in addition it covers certificate validation and certificate path processing with both CRLs and OCSP. Finally, it also covers using PKCS #12, processing CMS and S/MIME messages using the BC APIs, SSL using the JSSE, and gives an introduction as to how to use the Bouncy Castle ASN.1 library.
The book also has some on-line resources including code examples and a forum.
1 Mind you, you would probably have to read it first to be aware of this... ;-)
Practical Cryptography
Niels Ferguson, Bruce Schneier - John Wiley & Sons
Not so much a book about algorithms either, but a book about how to use them in a general sense. If you are looking at implementing a secure system, rather than just implementing basic cryptography this is a great book to read.
Java Cryptography Extensions : Practical Guide for Programmers
Jason Weiss - Morgan Kaufmann
Covers the JCE and some parts of the JCA as seen in JDK 1.4.
Wireless Java: Developing with Java 2, Micro Edition
Jonathan Knudsen - Apress
Includes a section on developing with the Bouncy Castle Lightweight APIs.

J2EE Security for Servlets, EJBs, and Web Services
Pankaj Kumar - Prentice Hall PTR
Includes sections on the JCE, JCA and implementing PKI systems with Java and a discussion of what goes on under the covers when you install the Bouncy Castle provider.
Applied Cryptography: Protocols, Algorithms, and Source Code in C (Second Edition)
Bruce Schneier - John Wiley & Sons
A general introduction to Cryptography, if you are new to this area it is well worth the effort to read a copy to gain some understanding of how cryptographic algorithms work.
Handbook of Applied Cryptography
Alfred J. Menezes, Paul C. Van Oorschot, Scott A. Vanstone - CRC Press
Considerably more academic than Bruce Schneier's book, really intended for people with a good background in mathematics and computer science. Very solid, coveringboth algorithms and basic number theory. Chapters for this book are also available on the web at http://www.cacr.math.uwaterloo.ca/hac/ with some restrictions.
Simple Authority
Newsletters
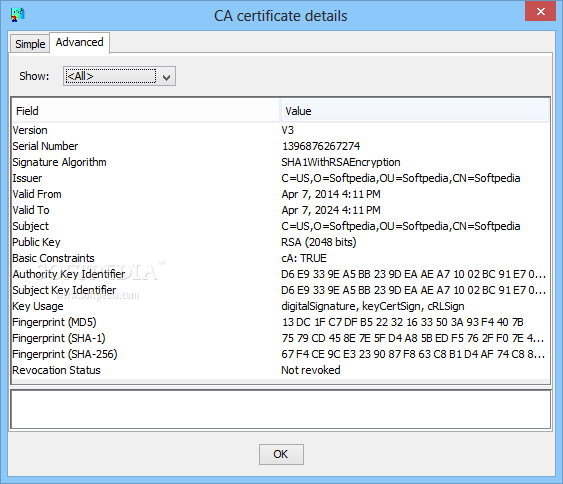
Sample Authority Note
English
Crypto-Gram
Free monthly e-mail newsletter on computer security and cryptography from Bruce Schneier.

Web Links

English
Unofficial Java Web Start/JNLP FAQ
If you are having trouble using cryptographic providers in conjunction with Java Web Start, this is the place to look first.
RSA Lab's Cryptography FAQ
Frequently asked questions about today's cryptography from RSA Laboratories.
The Object Identifier Registry
Online registry of ASN.1 Object Identifiers and what they are.
The X.509 Style Guide
Peter Gutmann's implementation notes for developers of X.509 certificates. Humourous as well as very useful, also contains referencesto other introductory material covering PKI and cryptography.




